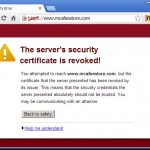
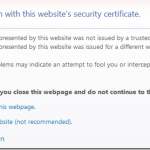
SSL-Certificate Revocation procedure. When is it required? Revocation of the certificate is often used by companies, when they want to replaced it. However, this decision is not correct. Revocation of SSL-certificate makes it unusable. Any web site or a server that…







Comments