Many people believe that SSL is the golden standard in network security. Yes, SSL helps protect you from different problems, but SSL communications can still be intercepted and disrupted. As it is, see this article. How exactly this happens, see this article.
Can the NSA to listen to the Internet? Many doubt that the NSA is really capable to intercept and break the SSL-protected Internet connection. In practice, NSA can do this.
It can make anyone, you do not need to look for specialists, hackers with supercomputers, etc. All you need – a credit card number.
There are many ways to attack SSL, but you do not need to get a fake SSL certificates, open a malicious certification authority or try MitM-attack. Why create yourself some problems, when you can just buy a proxy to intercept SSL? In example, ProxySG from Blue Coat Systems? The proxy does all the work for you.
Blue Coat, the largest company in the field of SSL interception is not unique in this area. There is a solution from Microsoft, such as Forefront Threat Management Gateway 2010. It, too, can do everything for you.
These services are nothing new. How do they work? To begin with, if you do not know how to operate the network, let us explain it.
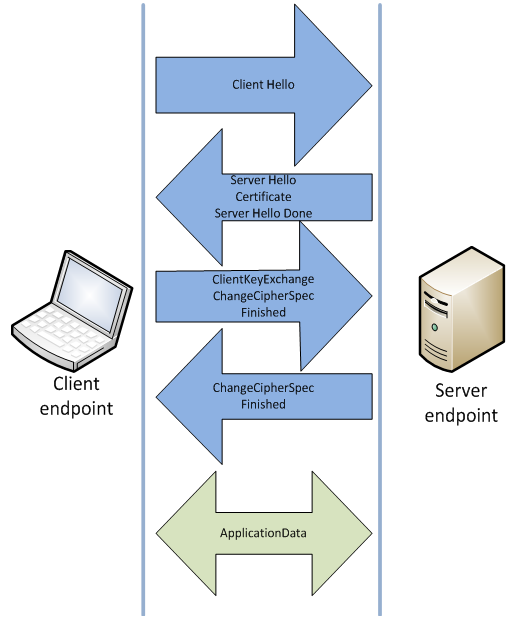
The client requests a secure connection and the server open handshaking process. Client is usually a Web browser, but it may also be the cloud, some type of network devices, etc. The client responds with which SSL type he can handle, and then server checks the cryptographic keys and certificates. All this is done until the server and the client does not establish a secure transport layer. Many believe that a secure connection is established in this point.
Maybe. But not always.
With the program for intercepting proxy that’s what happens in reality:
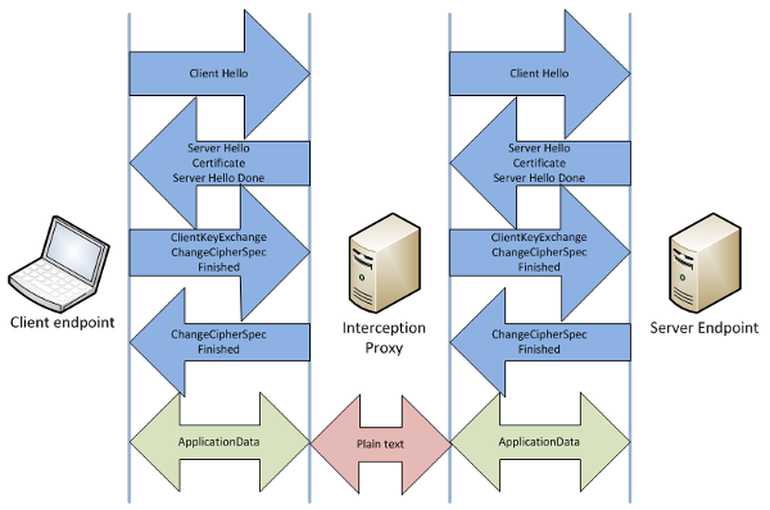
SSL proxy intercepts traffic between your computer and the Internet. When you go to the “secured” site, the proxy (not your browser) gets a real server certificate and creates a SSL-connection between it and the web servers. The client sent a digital certificate, which looks like a Web server certificate. As a result, it created a “safe” connection between the browser and the proxy server.
If you have properly configured proxy server, you will not see anything because they will register the internal SSL certificate of proxy server on your machine. This certificate will eventually be regarded valid. If not, you will get a pop-up message that if you click on “Continue”, will lead to the adoption of a forged digital certificate. In any case, you get a secure connection to the proxy server, and it has already received a secure connection to an external site. And everything that will go through a proxy can be read in plain text.
Even if your company can do it, why NSA can’t? But it is unlikely that NSA will analyze traffic and metadata of standard users. It is simply not required. Technically, they can do it, but in general it is simply not necessary.
Do you need SSL certificates? The store of certificates entrusted by years and millions of visitors — LeaderSSL. Buy a certificate from a trusted brand.


Comments