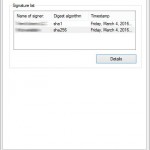
Rejection of the SHA-1 certificates had an impact not only on the owners of sites and software vendors, but also to malware creators. In a recent report, Symantec revealed information that company discovered a whole family of malicious programs that…

Comments