The spread of invalid certificates is wide enough. It is difficult to find anyone who has never encountered them. Here are some reasons that lead to such a wide spread of invalid certificates:
Incorrectly configured virtual hosting
Most sites now work on port 80, and do not use encryption. The biggest mistake of many hosting – placing of plain sites without encryption on the same IP-address as other sites, using encryption on port 443. As a result, users who want to access to the conventional site on the https protocol, get a completely different site. The certificate does not match the requested domain.
The problem is that, in technical terms, we have no mechanism for checking whether the site supports encryption. Placing simple sites correctly – is placing them on the IP-address with closed port 443.
Insufficient cover of names
In some cases, certificates are issued and deployed, but the site operator does not specify all required host names. For example, if you place the site www.example.com, a certificate must include the domain name, as well as just example.com. If you have other domains that point to a site, the certificate must include them, too.
Self-signed certificates and private CA
Such certificates are not trusted, because they are not suitable for public use. They are either self-signed or issued by a private certificate authority. Such certificates indistinguishable in public space from the certificates used to MITM attacks.
Why users apply such certificates? In fact there are many reasons. For example, the purchase, configuration and extension of certificates is a challenge. Not long ago, the certificates were quite expensive. Some people believe that public certificates should be free, and therefore do not buy them. However, only public certificates suitable for public sites.
Expired certificates
Another significant reason for the emergence of invalid certificates – their expiry. Site owners forget to renew their certificates.
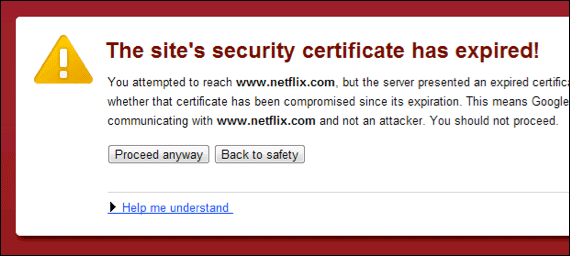
Expired certificate warning
Improper configuration
Popular problem – incorrect certificate configuration. In order to certificate was trusted, every user agent must have a trust chain, starting from the server certificate to a trusted root. Servers need to provide the whole chain, except of trusted root. Incomplete Chain – cause of problems with the certificate.
Do you need SSL certificates? The store of certificates entrusted by years and millions of visitors — LeaderSSL. Buy a certificate from a trusted brand.


Comments