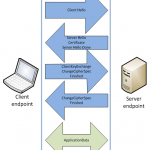
Many people believe that SSL is the golden standard in network security. Yes, SSL helps protect you from different problems, but SSL communications can still be intercepted and disrupted. As it is, see this article. How exactly this happens, see…

Many people believe that SSL is the golden standard in network security. Yes, SSL helps protect you from different problems, but SSL communications can still be intercepted and disrupted. As it is, see this article. How exactly this happens, see…

In the era of Apple vs FBI and large-scale hacking on a regular basis, many people are beginning to realize that our data are not so well protected as they should be. Google, Amazon, Facebook, Microsoft and many other technological…

Security researchers working for the company Sucuri, have decided to revise the report, written back in 2012, dedicated to the API-call security. API calls must verify the integrity of such libraries as JSSE, OpenSSL and of GnuTLS, or transport libraries…
Comments