
If your company – a major Internet project, you need an SSL certificate with Extended Validation. This certificate is the prestigious company attribute in the Internet – it allows you to set “seal of confidence” on website, confirming ownership of…

If your company – a major Internet project, you need an SSL certificate with Extended Validation. This certificate is the prestigious company attribute in the Internet – it allows you to set “seal of confidence” on website, confirming ownership of…
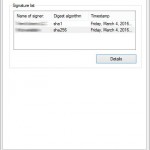
Rejection of the SHA-1 certificates had an impact not only on the owners of sites and software vendors, but also to malware creators. In a recent report, Symantec revealed information that company discovered a whole family of malicious programs that…

There are two popular protocol which works with sites: http – very simple, and https – the same as http, but with encryption. If you are using https site gets two benefits: Traffic between the user and the site cannot…

Data transfer over HTTPS does not give attackers: Intercept data, because they are transmitted over an encrypted channel. When data is transmitted in plaintext, they can be quite easily intercepted. For example, in the Wi-Fi networks – especially if the…

SSL-certificate renewal is often a rather complicated process. In this article we will describe some of the problems that you may experience when you renew the SSL-certificate (with Godaddy). To begin with I should say that I am not an…
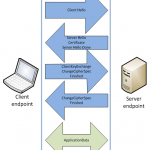
Many people believe that SSL is the golden standard in network security. Yes, SSL helps protect you from different problems, but SSL communications can still be intercepted and disrupted. As it is, see this article. How exactly this happens, see…

Using your own digital certificates to internal corporate networks, such as intranets and the VPN, enable your business to save a lot of money. Digital certificates form the basis for the infrastructure work technology of public key (PKI). These technologies…
Comments