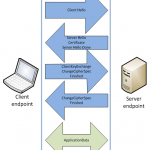
Many people believe that SSL is the golden standard in network security. Yes, SSL helps protect you from different problems, but SSL communications can still be intercepted and disrupted. As it is, see this article. How exactly this happens, see…

Many people believe that SSL is the golden standard in network security. Yes, SSL helps protect you from different problems, but SSL communications can still be intercepted and disrupted. As it is, see this article. How exactly this happens, see…

A common way to hack the site – get passwords to the administrative panel of the site. Basically passwords obtained in the following ways: intercept the password that has been transmitted through unprotected HTTP protocol; pick the password by brute…

CAs provides the SSL-certificate to owner of fake domains used in phishing against known online stores and banks. Just in a month attackers were able to obtain official security lock for hundreds of fake websites that are aimed at banks…
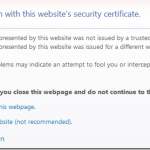
The spread of invalid certificates is wide enough. It is difficult to find anyone who has never encountered them. Here are some reasons that lead to such a wide spread of invalid certificates: Incorrectly configured virtual hosting Most sites now…

How to manage SSL-certificates to achieve effective protection of the web site? We will review current methods and established practices in this article. Having the installed SSL-certificate does not guarantee overall protection of your web site. Each SSL-certificate has its own private…
Comments