Rejection of the SHA-1 certificates had an impact not only on the owners of sites and software vendors, but also to malware creators. In a recent report, Symantec revealed information that company discovered a whole family of malicious programs that have been signed with two digital certificates. One certificate has SHA-1 signature, and the other backup certificate has SHA-2 signature.
This virus is called Carberp, it was discovered in recent spammer campaign in which were involved users from Denmark, Sweden, Israel, Ethiopia and the United States.
As speak security researchers, this trojan is one of the first cases where the malware have been signed with two certificates. It is caused by a general transition from unsafe SHA1 technology to a more secure standard SHA2.
We can expect that in the near future there will be a lot of Trojans, signed SHA1 and certificate SHA2
Technical reasons why malware using SHA2 are obvious. Many software manufacturers, including the Microsoft, whose products are often the target of hacker attacks, announced plans to end support for SHA1 certificates, starting from January 2016. In future the company plans to stop support SHA1 in their products.
Have reserve certificate SHA2 allows malware to roll back to a safe option if SHA1 certificate will lead to validation errors. Most likely, SHA1 will not be removed from existing malware, because it allows hackers to attack the old operating system, where the SHA1 is a main mechanism of digital signature. In such systems, SHA2 is not supported, and therefore they have attractive open vulnerability.
While virus creators have already implemented the transition to the system SHA2, some site owners still have problems with transition to SHA2. Just last month Mozilla released to their Symantec client nine new SHA1 certificates, which puts the most powerful security threats.
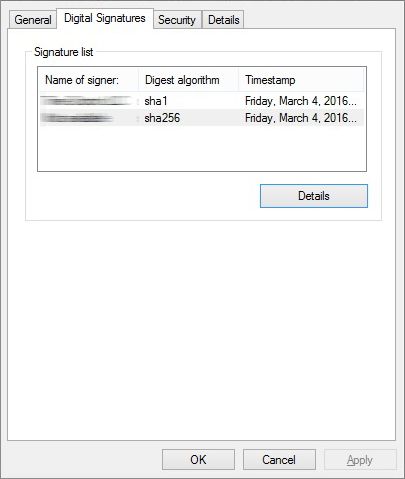
An example of a malicious program, which was signed immediately SHA2 and SHA1 certificate:
Do you need SSL certificates? The store of certificates entrusted by years and millions of visitors — LeaderSSL. Buy a certificate from a trusted brand.


Comments