The HTTPS protocol, which is a combination of standard data web protocol HTTP and cryptographic protocol SSL is almost the same age as “World Wide Web” in the form in which we know it. Based on the capabilities of traditional public key cryptography, it provides mutual (and in most practical applications – one-sided, that is only for the server) authentication to the Web server and client, cryptographic protection of the privacy of transmitted data and protect them from possible modification. The HTTPS protocol was designed with public PKI and the system root CA (Root CA).
Despite the fact that the HTTPS technology exist almost the same as the HTTP protocol, that it complements, certain classes of problems of its implementation have not been solved so far. Namely:
- Certificate Management implemented without taking into account the real needs of users (including ease of use).
- Implementation of SSL / TLS protocol may contain errors in realization and / or configuration.
- Current PKI standards are not maintained in the proper amount.
- Encrypted data is not available for inspection by network resources.
The question arises: can we consider these problems as the concerns with implementation of the protocol, if one of the items – the user interfaces problem, and the other – the fundamental property of the protocol? From a user perspective, all of these problems occur while using the HTTPS protocol in the Web browser.
SSL proxy technology
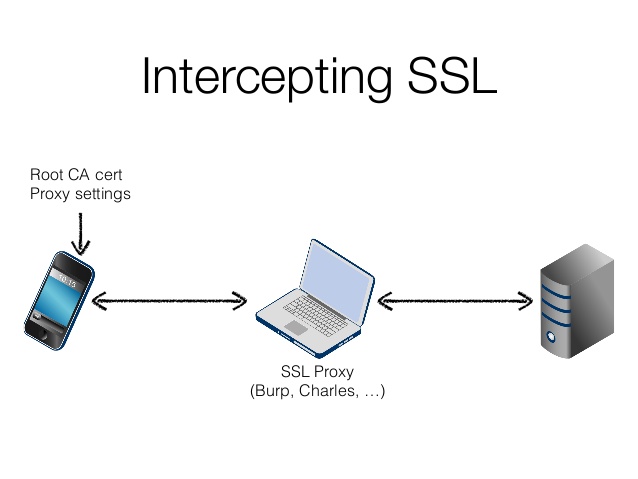
Ample opportunities for solving the above problems provides the implementation of HTTPS proxy technology.
Application proxies that implement SSL inspection using the method of “man in the middle”, currently spread quite widely. However, they specialize in the analysis of the contents of encrypted traffic (i.e., solve only fourth problem in the list above) and do not provide advanced features for managing certificates.
In a sense, it can be assumed that any “interference” in the operation of the SSL protocol is a violation of its ideology as a protocol that provides confidentiality, integrity and mutual authentication in a point-to-point.
In reality, however, in recent years, requirements to the HTTPS protocol have changed – just as the use of the HTTP protocol significantly escalated the level of fifteen years ago, when it was used only for the transmission of simple Web pages. In 1995 user sends on HTTPS only his credit card number, and protocol objectives is to protect against interception of data – now over HTTPS runs traffic of constantly used apps with a complex architecture (such as Gmail). Therefore, we must care must not only about the protection of confidential data but about the user has not get a virus through the web interface of the application and continued to receive adequate protection from other threats.
The algorithm of the proxy server, implemented by the method of “man in the middle”, is quite simple:
- The proxy server accepts the TCP-connection from the client and receives a command to establish a connection to the server.
- The proxy server sets the TCP-connection to the server and start the SSL-session.
- The proxy server receives information about the certificate, and makes its verification, the results of which either disconnects, giving the client a diagnostic error message, either generates a self-signed certificate, using his public key and service information from the server, and if necessary, signing his certificate by embedded Certification Authority.
- The proxy server starts SSL-session with a client using this new certificate.
- The proxy server receives the HTTP-request from a client, sends it to the contents inspection mechanism and, in the absence of errors and violations of security policy, sending to the HTTP-server.
- The proxy server receives a response from the HTTP-server transfers it to the contents inspection mechanism and, in the absence of errors and violations of security policy, sends to client.
Do you need SSL certificates? The store of certificates entrusted by years and millions of visitors — LeaderSSL. Buy a certificate from a trusted brand.


Comments